Uncovering the MAESTRO Toolkit: A Dangerous VM Escape Unraveled
In December 2025, an alert security team intercepted a group of hackers just in time, revealing a startling method of attack that compromised the very core of server security. Researchers Anna Pham and Matt Anderson from Huntress provided an in-depth analysis of how these attackers managed to escape from a virtual machine (VM) environment, infiltrating an entire host server. Their findings, disclosed to Hackread.com, unveil a sophisticated toolkit that may have operated undetected for years.
The Nature of Virtual Machines
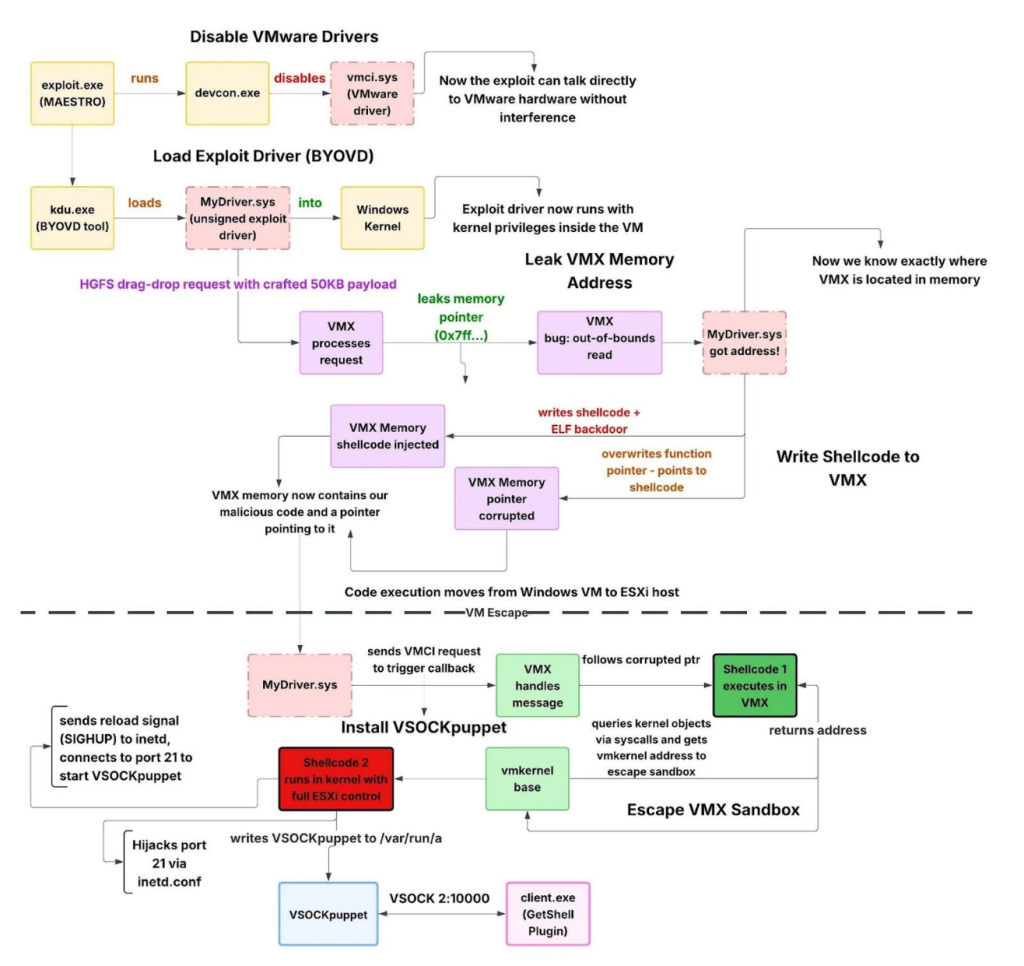
To understand this breach, it’s essential to grasp the concept of virtual machines. VMs are essentially isolated digital environments, comparable to individual rooms within a building. The expectation is that if one room suffers a security breach, the others remain unaffected. However, the researchers found that the attackers bypassed these protective barriers using a technique known as VM Escape. This method enabled them to leap from a guest VM directly into the host server’s core, known as the ESXi hypervisor.
How the Attack Started
The intruders didn’t employ any extraordinary skills to gain entry; instead, they utilized a stolen password to exploit a SonicWall VPN, a widely used tool for remote working. Upon infiltrating the system, they accessed a nefarious toolkit labeled MAESTRO.
Their method was calculated: the hackers targeted a crucial process dubbed VMX—the intermediary that allows the virtual machine to communicate with its host server for routine tasks, such as file transfers. By compromising this communication channel, the hackers could send direct commands to the main server. The attack was structured and meticulous; they even adjusted server settings to prevent it from contacting the security team for assistance while they navigated through the network to pilfer data. Notably, the MAESTRO toolkit demonstrated its prowess by being operational across 155 versions of VMware software, from 5.1 to 8.0.
The Zero-Day Vulnerabilities
What adds a layer of urgency to this incident is the timeline of discovery. Although VMware did address these vulnerabilities—identified as CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226—on March 4, 2025, it became apparent that the MAESTRO toolkit was already built as early as November 2, 2023. This highlights a grave reality: the attackers potentially exploited these zero-day vulnerabilities for over a year before being caught.
Digging deeper into the toolkit revealed annotations in simplified Chinese, including a directory translated as “All version escape – delivery.” This suggests the involvement of a well-resourced developer, suspected to be based in a Chinese-speaking region.
The Invisible Path: VSOCK Communication
One of the more insidious elements of this attack was the utilization of a unique communication pathway known as VSOCK. Unlike standard internet traffic commonly monitored by security tools, VSOCK acts as a clandestine tunnel within the machine, evading detection from traditional firewalls. This stealthy approach enabled the hackers to communicate with the server without raising alarms.
Recommendations for Organizations
In light of these revelations, the Huntress team emphasizes the urgent need for businesses to take proactive measures. Organizations must immediately patch their systems and scrutinize their servers for any unusual or suspicious activity. While this attack was thwarted before it could descend into a catastrophic ransomware incident, it underscores the critical need for continuous monitoring and vigilance, even within seemingly insulated environments.
By understanding the intricacies of this attack, companies can better prepare themselves against the evolving landscape of cyber threats. This incident serves as a timely reminder that in the world of cybersecurity, isolation does not imply safety, and the need for robust security practices is more important than ever.

