The Rising Threat of Cyber Extortion: Red Hat’s Recent Breach

Background on Red Hat’s Data Breach
In a striking development for enterprise software giant Red Hat, the company is currently facing a cyber extortion situation instigated by the Crimson Collective hacking group. Reports surfaced recently of a significant data breach that has prompted Red Hat’s internal teams to respond urgently. The breach involves the theft of approximately 570GB of compressed data from 28,000 internal development repositories.
This stolen data includes around 800 Customer Engagement Reports (CERs), detailing sensitive information about various customers’ networks, infrastructures, and platforms. As if the weight of the breach wasn’t heavy enough, the Crimson Collective has openly announced attempts to extort Red Hat into complying with their ransom demands, claiming that their outreach efforts were met with silence.
The Role of GitLab in the Breach
The breach specifically affected Red Hat’s GitLab instance, which serves as a platform for Red Hat Consulting to manage various consulting engagements. This detail underlines a critical point: even trusted systems, often employed within the layers of corporate governance, are vulnerable to cybercriminal activities. The attackers reportedly claimed that the potential fallout from this breach could compromise the integrity of systems for global corporations, citing organizations like Walmart, American Express, and the Department of Defense among others.
New Alliances in Cybercrime
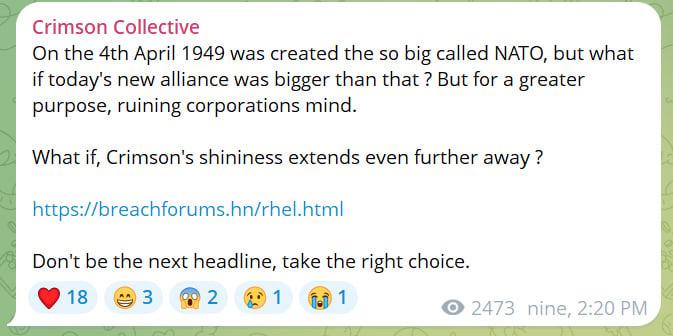
While the Crimson Collective initially operated independently, they have since partnered with another group known as Scattered Lapsus$ Hunters. This alliance was announced through a message on their Telegram channel, suggesting an organized approach to extortion that resembles a network of criminals collaborating for maximum effect.
In a rather dramatic proclamation, they liken their new alliance to a high-stakes geopolitical move, dubbing it the formation of a larger coalition aimed at disrupting corporate stability worldwide. This raises important questions about the evolution of cybercrime and the increasingly structured nature of these digital rogues.
Source: BleepingComputer
The Extortion Landscape
As the situation evolves, the ShinyHunters data leak site has emerged as a tool for the Crimson Collective to leverage their stolen data further. According to announcements from the hackers, unless Red Hat negotiates a ransom, the leaked data is set to be made publicly available by October 10.
This development underscores the alarming reality of extortion-as-a-service (EaaS), a model where multiple criminal groups collaborate to amplify their cyber extortion efforts. Reports indicate that ShinyHunters has acted as a broker, orchestrating extortion efforts on behalf of other groups, thus commodifying the very act of extortion.
ShinyHunters’ Operations and Implications
Emerging as a significant player in the world of cyber extortion, ShinyHunters has been linked to several high-profile incidents over recent months. Reports have suggested that they operate based on revenue-sharing models where they take a portion of the extorted funds, mirroring the ransomware-as-a-service (RaaS) framework. The idea is simple: by working collectively, these groups can maximize their gains through organized efforts rather than operating in solitude.
Their ongoing manipulation of high-stakes data breaches implies that organizations may need to rethink their cybersecurity strategies comprehensively. The repeated references to ShinyHunters in various attacks, including those targeting Oracle Cloud and educational data from PowerSchool, showcase how widespread this threat has become.
Conclusion: Security in a New Era
The ongoing situation with Red Hat serves as a reminder of the growing complexity of cyber threats that organizations face today. As sophisticated as enterprise security infrastructures may be, they often find themselves vulnerable to the latest attacks perpetrated by groups organized along lines reminiscent of businesses themselves.
With major players such as ShinyHunters now taking center stage, the imperative for companies to adopt advanced cybersecurity measures and prepare for potential breaches has never been greater. As we look ahead, it will be critical for organizations to remain vigilant and proactive in safeguarding their data against these evolving and structured cyber threats.

