The System-Centric Blind Spot in IEC 62443
For nearly two decades, the IEC 62443 framework has been a cornerstone of industrial cybersecurity, shaping the way organizations approach the protection of their operational technology (OT) environments. This framework, along with influential models like Gartner’s OT model, has fostered a system-centric architecture that emphasizes zones, conduits, and system roles as the primary means of security design. While these elements are essential for reducing attack surfaces and increasing attack distances, they reflect a perimeter mindset that is increasingly inadequate in today’s interconnected industrial landscapes.
The Limitations of a System-Centric Approach
The IEC 62443 framework was initially developed during a time when control systems operated in relative isolation, protected by a limited number of network barriers. However, the reality of modern industrial environments is starkly different. Today, process automation systems are not only interconnected but also engage with a myriad of external systems, including diagnostic tools, business applications, cloud services, and optimization engines. These interactions often bypass traditional zone boundaries, creating implicit trust paths that can compromise security.
The fundamental issue with the IEC 62443 framework is that it prioritizes controlling access over understanding how control functions influence one another across various layers and domains. This oversight can lead to significant blind spots, particularly in converged environments where IT, OT, and business functions interact fluidly. The framework’s focus on static network boundaries fails to account for the dynamic nature of modern industrial systems, where segmentation alone does not adequately mitigate process exposure.
Control Proximity: A New Lens for Risk Assessment
To address these shortcomings, it is crucial to shift the focus from a system-centric to a process-centric approach. At the heart of this transition is the concept of control proximity—the degree to which a function can directly or indirectly influence physical process behavior. Control proximity provides a more nuanced understanding of risk, capturing the real-world implications of a system’s ability to affect safety, quality, or operability if compromised.
By evaluating exposure through the lens of control proximity, organizations can move the conversation from merely protecting infrastructure to understanding operational consequences. This shift necessitates a reevaluation of existing risk assessment frameworks, such as the Controllability-Observability-Operability (COO) model, which is better suited for cyber-physical risk than the traditional CIA triad.
Gaps in IEC 62443 for Converged Environments
While IEC 62443 offers a structured approach to cybersecurity, its foundation remains system-centric, focusing on static boundaries and predefined roles. This creates significant gaps in risk identification and security requirement allocation, particularly in environments where traditional perimeter definitions no longer align with functional influence and trust relationships.
Security Requirement Allocation
IEC 62443-3-3 defines security requirements for systems but does not incorporate the concept of control proximity into its security level (SL) definitions. For instance, a function with high control proximity—such as one capable of altering setpoints—may require a higher security level even if its network exposure is minimal. The framework’s foundational requirements focus on who can access or use a function, neglecting the importance of functional authority and the context in which a function operates.
Risk Identification
IEC 62443-3-2 outlines a risk assessment process rooted in a system-centric structure, emphasizing asset identification and zone modeling. However, it lacks mechanisms to analyze functional influence and control proximity, resulting in risk models that reflect static network visibility but miss functional exposure. This oversight can lead to misaligned security priorities that do not adequately address actual process risks.
From Technical Boundaries to Functional Exposure
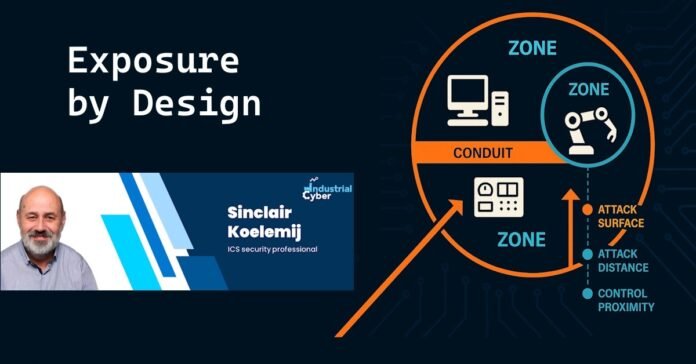
To effectively secure cyber-physical systems, organizations must understand security as a combination of exposure, robustness, and resilience. Exposure, in particular, defines the likelihood and ease with which a system can be targeted or misused. It must be redefined as a function of three critical factors: attack surface, attack distance, and control proximity.
- Attack Surface: The number of interfaces or services that are reachable by an attacker.
- Attack Distance: The extent to which an attacker must penetrate the system to reach a target.
- Control Proximity: The degree to which a function can influence physical process behavior.
This triad provides a realistic view of cyber-physical exposure, allowing organizations to recognize trade-offs and vulnerabilities that may not be apparent through traditional risk assessments.
The Need for a Functional Trust Model
While IEC 62443 provides essential technical controls for authentication and access management, it lacks a model that evaluates whether a system should influence another based on its role in the process. Traditional OT security risk analysts often focus on mapping attack paths confined to digital automation systems, while cyber-physical risk analysts extend this view to include control influence paths—chains of functional trust that dictate how one function affects another.
The Rings Of Protection Analysis (ROPA) 2.0 methodology enhances existing risk-assessment frameworks by incorporating control influence paths, enabling analysts to compute an overall Probability of Failure if Attacked (PFA). This approach allows for a more comprehensive understanding of risk, tying exposure directly to the dynamics of the control environment.
Evolving Toward Operationally Aligned Cybersecurity
In modern industrial systems, security must be intrinsically linked to operational integrity. This requires organizations to:
- Map not just access rights, but also functional roles, control proximity, and trust boundaries.
- Enforce functional legitimacy, ensuring that systems are contextually allowed to act based on their roles in the process.
- Apply exposure modeling that combines attack surface, attack distance, and control proximity.
- Trace both attack paths and control influence paths across layers and domains.
By adopting this control-centric view, organizations can assess exposure based on operational consequences rather than mere compliance with static security measures. This shift redefines what constitutes a valid risk control, emphasizing the need for constraints on control influence that are explicitly designed, implemented, and validated.
Conclusion
The IEC 62443 framework has provided a valuable foundation for industrial cybersecurity, but it is time to evolve beyond its system-centric limitations. By embracing a process-centric approach that prioritizes control proximity and functional authority, organizations can better align their cybersecurity strategies with the realities of modern industrial environments. This transition is not merely an enhancement of existing practices; it is a fundamental shift in how we understand and manage cyber-physical risk.
To move forward, organizations must analyze existing ICS designs for control influence paths, assess process-level trust relationships, and incorporate dynamic hazard scenarios into their risk modeling. By doing so, they can ensure that their cybersecurity measures are not only compliant but also effective in safeguarding operational integrity in an increasingly interconnected world.